Bomb Detector Security Scanners: An Overview
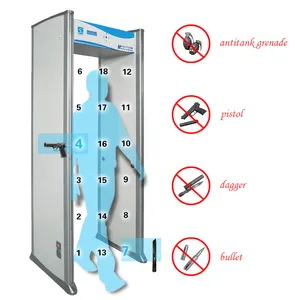
Ensuring the safety of residential and commercial spaces is paramount in today's world. Bomb detector security scanners are sophisticated devices designed to detect a range of explosive materials and devices. These systems play a crucial role in maintaining security and peace of mind.
Types and Applications
The variety of bomb detection equipment caters to different scenarios, from handheld units for individual checks to larger, more complex systems for securing premises. Applications span across various sectors, including transportation hubs, corporate buildings, shopping centers, and public events, ensuring a versatile approach to security.
Features and Materials
Modern explosive detection systems are equipped with advanced features such as high sensitivity sensors, user-friendly interfaces, and durable materials that withstand various environmental conditions. These systems often incorporate state-of-the-art technology to accurately identify threats without causing false alarms.
Advantages of Integration
Incorporating security scanning devices into a security protocol offers numerous advantages. They serve as a deterrent to potential threats and provide a systematic approach to safety. Their integration with other security measures creates a comprehensive safety net for any facility.
Customization and Adaptability
The adaptability of security scanners allows for customization according to specific security needs. Whether the requirement is for a discreet system or one that offers visible deterrence, these devices can be tailored to suit various environments and threat levels.
Choosing the Right System
Selecting the appropriate bomb detection system requires consideration of several factors, including the size of the area to be secured, the volume of people, and the level of threat anticipated. With a range of options available, it is possible to find a system that aligns with specific security requirements.


































 浙公网安备 33010002000092号
浙公网安备 33010002000092号 浙B2-20120091-4
浙B2-20120091-4